Google recently introduced an interesting technology called sidewiki. The tool allows you and everyone else on the internet to craft and maintain annotations about web pages each sidewiki entry is associated with through the use of simple-to-use browser plugin or related tools. How could this possibly relate to security? Pages could be marked by people or programs that detect when they include phishing, cross-site-scripting, or other malicious vulnerabilities. With some careful forethought, these markings could use a documented system which would facilitate people and browser plugins to act on those notations, and thereby help to prevent users from becoming victims.
|
||||
|
News
|
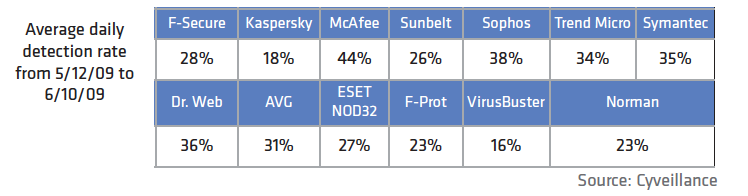
Your antivirus software, according to this new report from Cyveillance.
Look at that chart! Chances are very good that if you have antivirus software running on your computer, it comes from one of the companies listed there. Where’s Norton? Sorry cowboy, Norton is made by Symantec. These results are atrocious. Would you use your browser if two out of three times that you clicked on a link it took you to the wrong page? Would you buy a car that only started every third time? OK, I actually owned a car like that in my younger days, but I digress. Supervisory Control And Data Acquisition (aka SCADA) devices have evolved over time to be capable of being attached to the Internet. These devices are at the heart of most critical infrastructure control. For a while now, I have been trying to understand why people involved in utilizing SCADA devices consider it acceptable to connect them to the Internet. In discussions with various people that have knowledge of many such systems, I have been surprised to learn that it is common practice for the networks to include connectivity to the Internet. Firewalls of various types are employed to theoretically address the concern that malicious people may find ways to access and control these systems, possibly leading to life-threatening situations. Last week, IBM released its Mid-Year Trend and Risk Report. In the report, they remark that phishing had fallen dramatically in the last six months. Of all the spam sent, phishing now only represents 0.1%. Does this mean that the security industry has solved the phishing problem? If only it were so. One-tenth of one percent. One in a thousand. A minuscule amount. Minuscule that is until one stops to consider just how much spam gets sent on a daily basis. How much is that? Estimates vary. Let’s assume that spam volumes haven’t changed much in the past 16 months. This means that over 100 billion pieces of spam are sent every day. There is little question that botnets have become a huge problem for abuse and security professionals. In many cases to date, experts that are attempting to provide relief from the activities of the botnets have focused on dismantling the botnet command and control systems. The question that I raise here is whether doing anything beyond identifying the command and control systems is productive? I recognize that valid arguments exist from multiple perspectives, and also believe that no one answer is universally best for all situations. That said, I am leaning in the direction that combating the effects of botnets would benefit given robust identification of but not the dismantling of command and control systems. One of my colleagues today referred me to this excellent posting about password recovery speeds. Reading through the posting it became very clear to me just how achievable it is for crackers to brute-force determine pass-words/pass-phrases given crypted text, commonly used within the majority of password storage mechanisms employed today. Even easier would be PIN numbers for ATM and SIM cards, given the limited set of digits from which to select. My conclusion is that it borders on nearly impossible to craft a pass-word/pass-phrase that the cracker would not be able to recreate in a fairly short period of time, given the encrypted representation. On behalf of the staff here at Umbra Data, let me welcome you to our blog, Dark Side Intelligence. We will share our insights into what is happening in the world of malware, cybersecurity, cybercriminals, and the like. In essence, if it’s interesting to us and we also think it might be interesting to you, we’ll post it here. |
|
||
|
Copyright © 2008-2011 Umbra Data, Inc. • All Rights Reserved |
||||